
Cybersecurity: Internet security 101: Six ways hackers can attack you and how to stay safe - The Economic Times

Attacking A Virtual Toaster: An Experiment Shows How Quickly The Internet Of Things Can Be Hacked : All Tech Considered : NPR
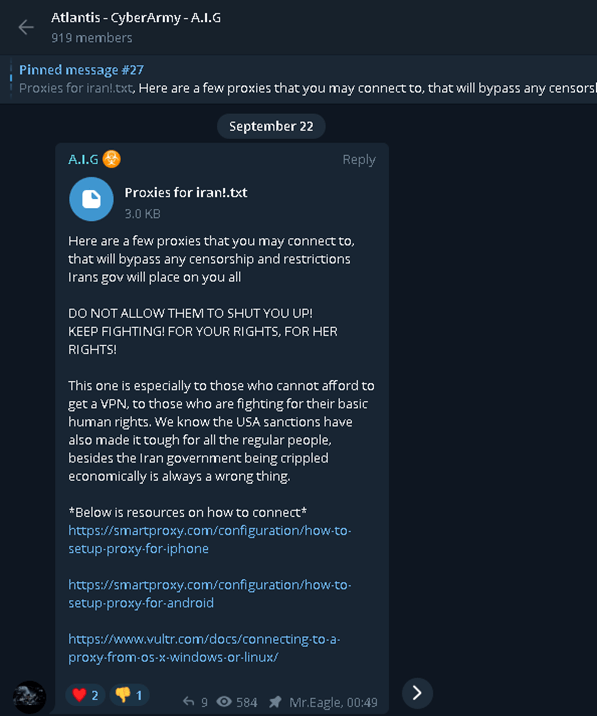
Hacker Groups take to Telegram, Signal and Darkweb to assist Protestors in Iran - Check Point Software

Which? on Twitter: "🚨How this WhatsApp scam works 1. You get text 2. Then a WhatsApp message from a friend asks you for the code. DO NOT SEND Your friend's WhatsApp has








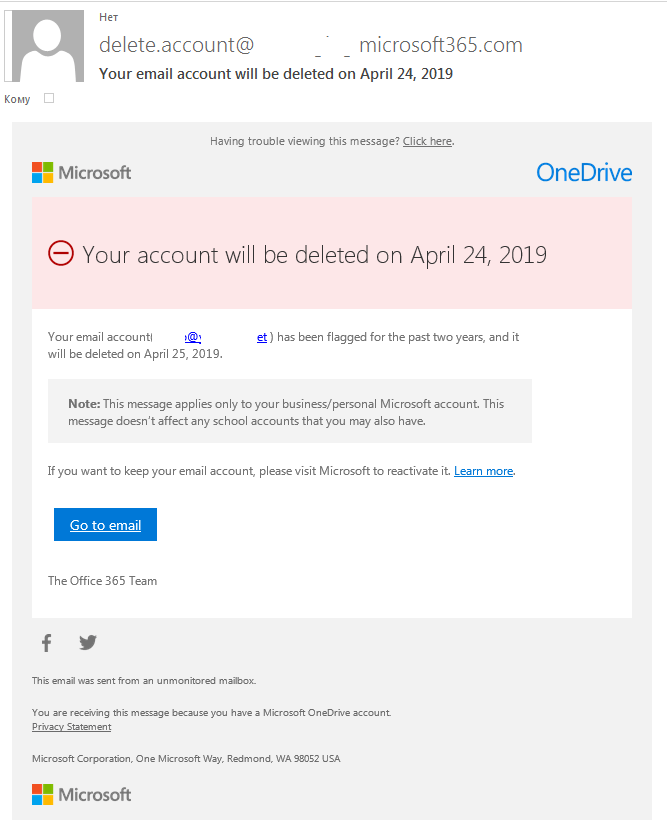
/cloudfront-us-east-2.images.arcpublishing.com/reuters/EV62MSSML5MZ5ANBN5SMOKKPDM.jpg)


